CapLoader 1.9.4 Released

A new version of our advanced PCAP filtering tool CapLoader was released today. The new CapLoader 1.9.4 release includes features like JA3 hash extraction from TLS traffic and a fantastic thing called Select Similar Flows, which is a unique feature that you will only find in CapLoader! We have also included a VXLAN parser, so that flows tunneled inside of overlay networks can be presented directly in the CapLoader GUI.
Select Similar Flows or Services
If you right-click a flow or service in CapLoader you’ll now be presented with an option to “select similar flows” (or services). This feature causes CapLoader to read through the loaded PCAP files again in order to find other flows that are similar to the one that was right-clicked. CapLoader doesn’t care about IP addresses or port numbers when assessing this similarity. Instead it looks at behavioral patterns in the traffic itself, such as packet sizes and byte patterns. In practice, this feature will select flows that are communicating using the same protocol as the one you clicked, regardless of which port it runs on. CapLoader already comes with an advanced feature for doing port-independent protocol identification, which currently detects over 170 protocols. But the “select similar” feature can even be used to find odd or proprietary protocols that aren’t in CapLoaders protocol database.
There is also a feature called “select VERY similar flows” which, instead of searching for flows with the same protocol, looks for flows with the same implementation or dialect of that particular protocol. This feature can be used to single out the network traffic of a particular software or tool from a haystack of network traffic from multiple applications, which all run the same application layer protocol. Another use case is to find additional malicious C2 sessions that run on top of a standard protocol like HTTP, TLS or DNS – provided that you’ve located at least one such malicious flow or service.
JA3 and JA3S Hashes for TLS Flows
We added JA3 extraction to NetworkMiner back in 2019, with the release of NetworkMiner 2.5. It’s now time to bring this useful little TLS fingerprinting feature into CapLoader as well. As of version 1.9.4 CapLoader attempts to extract JA3 and JA3S hashes from all TCP flows. The JA3 and JA3S hashes are presented in the Flows and Services tabs as separate columns. This allows users to filter flows based on a JA3 hash directly in CapLoader instead of having to export a filtered PCAP to an external tool to calculate JA3 hashes.
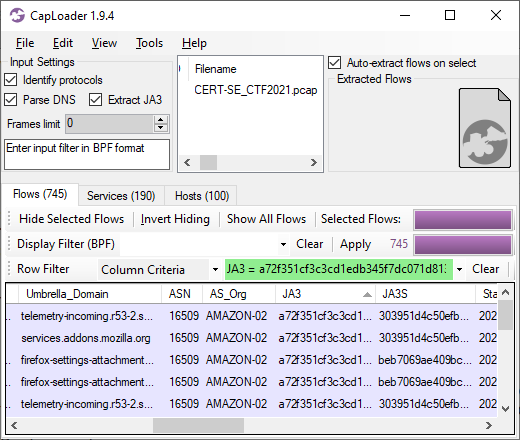
Image: Column criteria filter “JA3 = a72f351cf3c3cd1edb345f7dc071d813” on PCAP from CERT-SE’s 2021 CTF.
Extraction of Flows Inside of VXLAN Tunnels
VXLAN is a network virtualization technology that can be used to create overlay networks, where Ethernet frames are encapsulated inside of UDP packets (see RFC 7348). The UDP port used for VXLAN is 4789 or 8472. We added support for VXLAN to NetworkMiner in 2017, but CapLoader has until now only presented the VXLAN tunnels in the GUI when VXLAN traffic is loaded. We’re happy to announce that CapLoader now extracts flows for the VXLAN tunnels and the traffic inside of those tunnels.
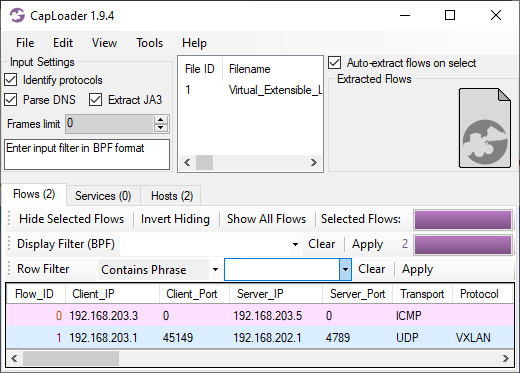
Image: ICMP flow extracted from VXLAN tunnel. PCAP file is Virtual_Extensible_LAN-VXLAN.pcap from Xena Networks
Additional GUI Improvements
We’ve also made several minor improvements to CapLoader’s user interface, such as a “Save Visible Flows” option on the File menu, which can be used to save the filtered traffic in the current view to a PCAP file. Another nice addition is the “Copy from Selected Rows” menu option, which can be used to copy text from a particular column.
CapLoader’s OSINT lookup context menus have also been updated to include some very useful services like Feodo Tracker, Hatching Triage and IPVoid.
Free Trial versus Full Version
Many of the new additions to CapLoader are only available in the full version, but the VXLAN extraction and some of the GUI additions are also available in the free trial version of CapLoader. No registration is required to download the trial — just download, extract and run for 30 days. If you like it, then please consider purchasing the full version!
Updating to the Latest Release
Users who have already purchased a license for CapLoader can download a free update to version 1.9.4 from our customer portal.
Posted by Erik Hjelmvik on Thursday, 16 June 2022 11:44:00 (UTC/GMT)
Tags: #CapLoader #JA3 #JA3S #Protocol Identification #Protocol Detection #PCAP #TLS #VXLAN



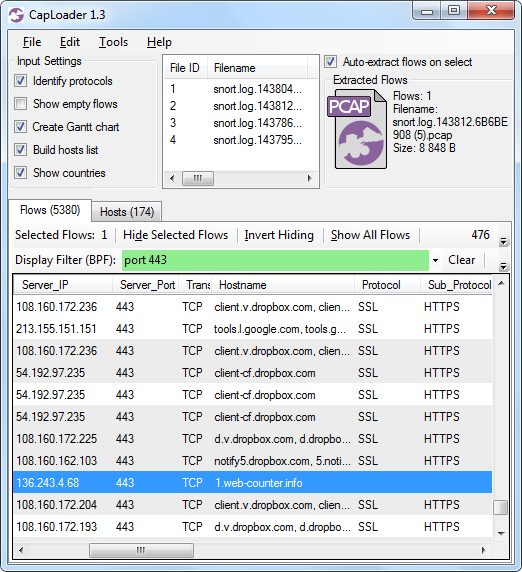 Image: Miuref/Boaxxe Trojan C2 traffic to "1.web-counter[.]info" on TCP 443 doesn't use SSL (or HTTPS)
Image: Miuref/Boaxxe Trojan C2 traffic to "1.web-counter[.]info" on TCP 443 doesn't use SSL (or HTTPS)


